Your last line of defense
Uncover novel and elusive vulnerabilities other controls miss.
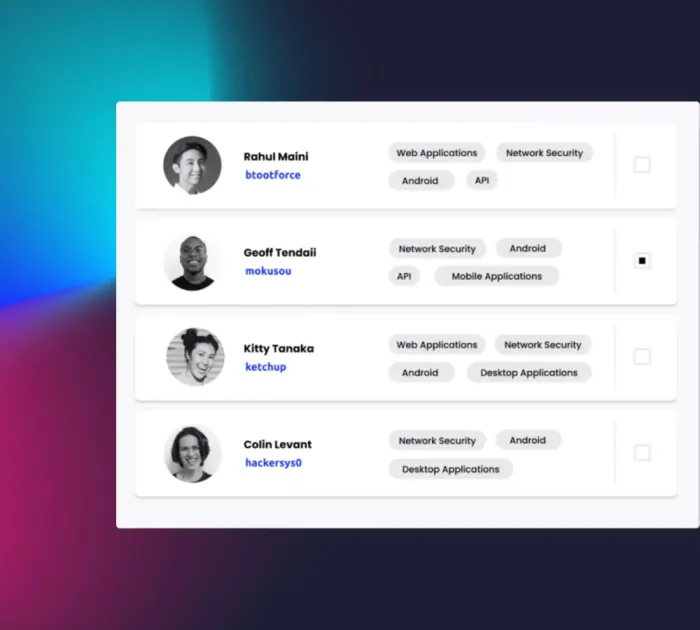
Attract hacker talent
Streamline communication and make your program stand out to attract the best talent in the field.
- Quickly onboard skilled hackers, reducing the time it takes to find and fix critical vulnerabilities.
- Select ID-verified and background-checked ethical hackers to assess external or sensitive internal assets.
- Direct hacker attention to new product and feature releases with time-bound bounty incentives and targeted testing options, including Spot Checks
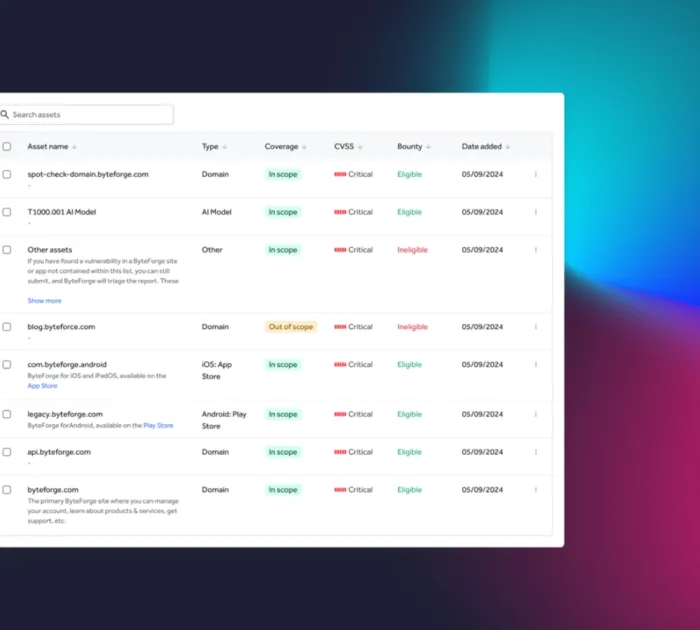
Centralized management for full control
A centralized interface provides organization-level asset management of in-scope assets across your bug bounty program and other HackerOne engagements
- Manage the life cycle of vulnerability reports - from initial hacker submission to remediation - all in one place.
- Ensure transparency via critical details such as bounty tables, disclosure guidelines, and safe harbor statements.
- Facilitate and track payments to hackers using our global payments infrastructure, and even award hackers with your own swag or merchandise in addition to monetary bounties.
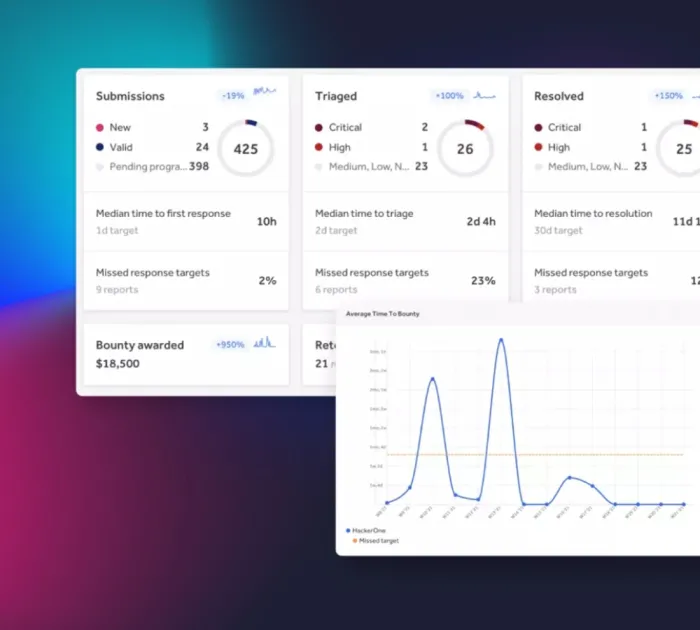
Program insights at your fingertips
Gain a complete view of performance with customizable insights and real-time data. Easily manage submissions, rewards, and researcher engagement for optimized outcomes.
- Track and display key program data such as submissions, rewards, researcher activity, and response times.
- Simplify report management, researcher interactions, and report resolution, all in one place.
- Compare your program’s performance across the HackerOne Platform with benchmarks against peers and industry standards.
Technology to scale your program
Speed up vulnerability remediation with AI, in-platform automations, and seamless integrations.
- Hai delivers actionable remediation advice and generates concise report summaries, helping your team act quickly on vulnerabilities and stay focused on key security tasks.
- Use prebuilt templates or customize workflows to automate common tasks like vulnerability routing and report life cycle management, improving both efficiency and accuracy.
- Take advantage of 30+ bidirectional integrations, ensuring findings flow directly into your existing workflows for faster and more effective remediation.
Triage services
Our in-house security analysts validate and prioritize all incoming vulnerability reports and maintain ongoing communication with hackers—zeroing out the noise while providing actionable insights to your team.
Security advisory services
Manage and scale your program with best practices and insights from experts in cyber risk reduction. Our solutions architects help tailor your program—from custom workflows to KPIs for measuring program success.
Frequently asked questions
A bug bounty platform connects your team with a global community of security researchers for continuous vulnerability discovery. This approach uncovers real-world risks that automated tools and internal teams often miss, helping you stay ahead of evolving threats.
A bug bounty program maximizes ROI by directing spending toward valid, high-impact vulnerabilities that actually reduce risk. You can measure this through Return on Mitigation (RoM), a metric that shows how every dollar invested leads to meaningful risk reduction and security improvements, making it easy to justify and track your investment over time.
Researchers are evaluated by skill, accuracy, and impact, with ongoing reputation scoring, activity monitoring, and optional controls like ID verification, profile labels, NDAs, or background checks to ensure quality and accountability.
Submissions go through AI and expert review to filter out duplicates and noise, so only validated, actionable reports reach your team. This process accelerates remediation and reduces wasted effort.
Yes. You define program guidelines with options to restrict researcher participation by skill or location, and add custom requirements for sensitive assets. Programs can run privately or publicly, adapting to your risk profile.
Bug bounty programs complement penetration testing and other security measures as part of a defense-in-depth strategy. Continuous, incentive-driven testing from a global community helps uncover real-world risks between scheduled assessments, delivering broader coverage and ongoing validation as your environment changes.
- Most engaged researcher community: More active researchers, more findings, and faster results.
- Faster, more accurate triage: Hai Triage provides a unique intake system combining AI to prioritize critical risks and reduce noise with human-in-the-loop oversight.
- Hai, HackerOne’s AI Security Agent: transform vulnerability management workflows by combining deep report analysis with real-time performance insights. Instantly grasp vulnerability report details, spot trends, and make faster, smarter decisions.
- Deep, actionable insights: Benchmarks, recommendations, and analytics drive business value, while automations streamline security operations and reduce manual work.
- Expanding integrations: Connect with your security stack quickly with 30+ bi-directional integrations with security and development tools so findings flow directly into existing workflows for faster remediation.